Nov 20 2024
8 min read

Effective and secure internal communication is the backbone of any organization. Every message or piece of information sent within a company can either be a point of strength or a potential vulnerability.
Data breaches are not a thing of the past, with major brands like Apple, Meta, and Twitter facing cybersecurity issues over the years. In August 2024, National Public Data (NPD) suffered a breach that exposed the sensitive information of over 2.9 billion people , affecting almost the entire U.S. population.
To avoid such risks, businesses must use tools with industry-grade security. Even something as simple as an internal communication tool or digital signage software must pass strict security certifications. This blog explores secure internal communication and how businesses can protect their sensitive data.

Secure internal communication ensures the safety and security of all the information exchanged between your internal team, departments, and the organization. It includes various methods and protocols used within the organization to protect data from unauthorized access, interception, or tampering.
The security gateway can face potential threats of phishing attacks, insider leaks, malware, data interception, and network security issues. Therefore, businesses should have strong security protocols, encryption, and a secure information exchange environment.
Moreover, secure internal communication verifies the identity of the user trying to access. This foundational principle of identity verification is critical for any digital system, including ensuring effective digital signage networks user management, where controlling who accesses and alters content is paramount. Someone with permission to access the information or decryption key can read and decipher it.
Also read: Best internal communication strategies for your workplace
The growth and success of a business heavily rely on information. A breach of confidentiality can leak important trade secrets, strategies companies hold, and valuable assets. Not only can it lead to a financial loss for a business, but it may also hamper the trust between employees and clients.
By securing internal communication channels, organizations can safeguard their assets, reputation, and long-term success. There are countless big brands that face the consequences of leaks of information, and the payback is also heavy.
Secure internal communication is crucial for organizations for several key reasons:
Protection of sensitive information: Businesses often deal with sensitive information such as employee data, trade secrets, and even clients’ private information. Businesses have to protect this information from unauthorized access. Data breaches or theft can hamper a business’s financial performance, reputation, and trust.
Compliance with regulations: Businesses are required to follow strict regulations regarding data protection and privacy. Industries, such as healthcare (HIPAA), finance (GDPR, PCI DSS), and government have provisions of penalties, legal actions, and loss of certifications if they fail to comply with security standards.
Maintaining trust and reputation: A secure internal communication system helps maintain the trust of employees, clients, and stakeholders by safeguarding their sensitive data. The organization’s reputation and reliability depend on how seriously it approaches data protection through its actions.
Avoiding financial loss: Information leaks or data breaches can lead to significant financial loss. Businesses and institutions have to bear the cost of reputational damage (remediation, legal fees, regulatory fines, and lost revenue).
Enhancing operational efficiency: Information as a key aspect of a business will trigger a disturbance in the other normal functions of the company. It leads to the fear of loss in productivity, innovation, growth, and overall operation efficiency.
This is particularly evident in how robustly managed communication tools, like those used for digital signage in US companies for better communication, streamline operations and ensure seamless information flow, preventing disruptions and boosting productivity.
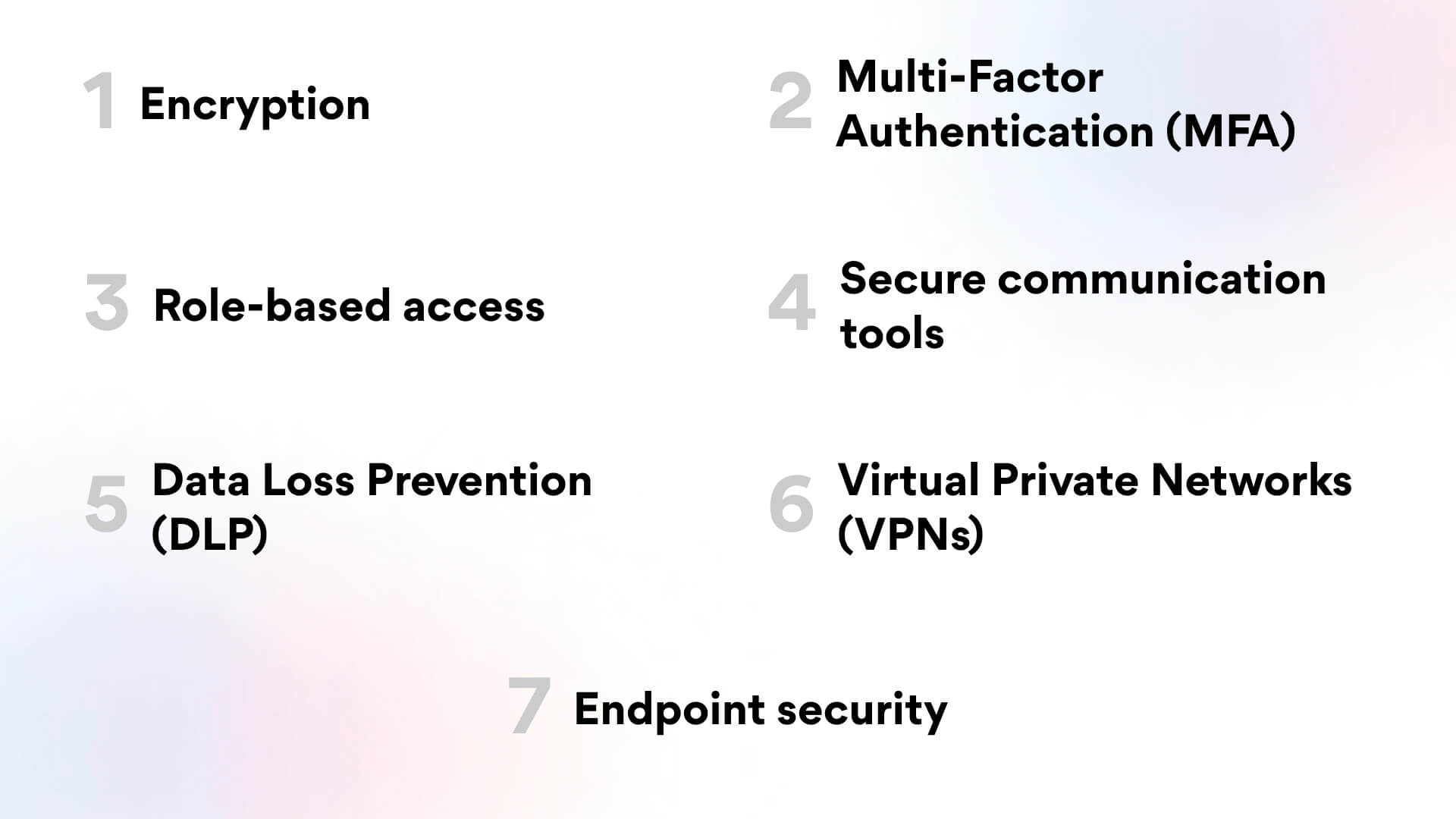
There are various methods that can be implemented in a layered security approach to provide secure internal communication in an organization:
Encrypt the readable data using a cryptographic algorithm to protect it from unauthorized users. Use end-to-end encryption for all the internal communication devices, or use devices with this facility to ensure privacy. The company must ensure that a standard encryption system, like AES (Advanced Encryption Standard) , is implemented with 256-bit keys for strong protection.
Implement Multi-Factor Authentication (MFA) allows users to go through more than once to verify their identity before accessing the information. The MFA can be a combination of a password (something you know), a physical token or device (something you have), or biometric verification (something you are).
Also read: Top internal communication tools to enhance modern workplace communication
Access control ensures that a user can access only specific information according to their role in the organization. For instance, an editor can’t have access to the information available to an admin. This role-based access control can be an effective way to protect data at different levels.
A communication tool that offers end-to-end encryption is a safer medium of communication. An ideal tool is one with secure file-sharing options and user authentication and adheres to security standards (like ISO, SOC-2). As digital signage software becomes more common in business, protecting these internal communication channels from leaks is more important than ever. Use tools like Pickcel, a SOC2- and ISO-certified digital signage software, which offers enterprise-level digital signage security features to ensure protection.
Pickcel makes it simple for businesses to showcase team meetings, project updates, or bulletin boards. The software offers a highly secure medium to integrate with business intelligence platforms and present dynamic dashboards and reports.
Check out: Pickcel's corporate digital signage solution for all your workplace communication requirements
Businesses can use a DLP solution to monitor and control the sensitive data within the organization. It can be enforced to analyze data patterns and immediately block the data transfer if it violates security policies. Organizations can set their security policies and use DLP tools to identify unauthorized data transfer.
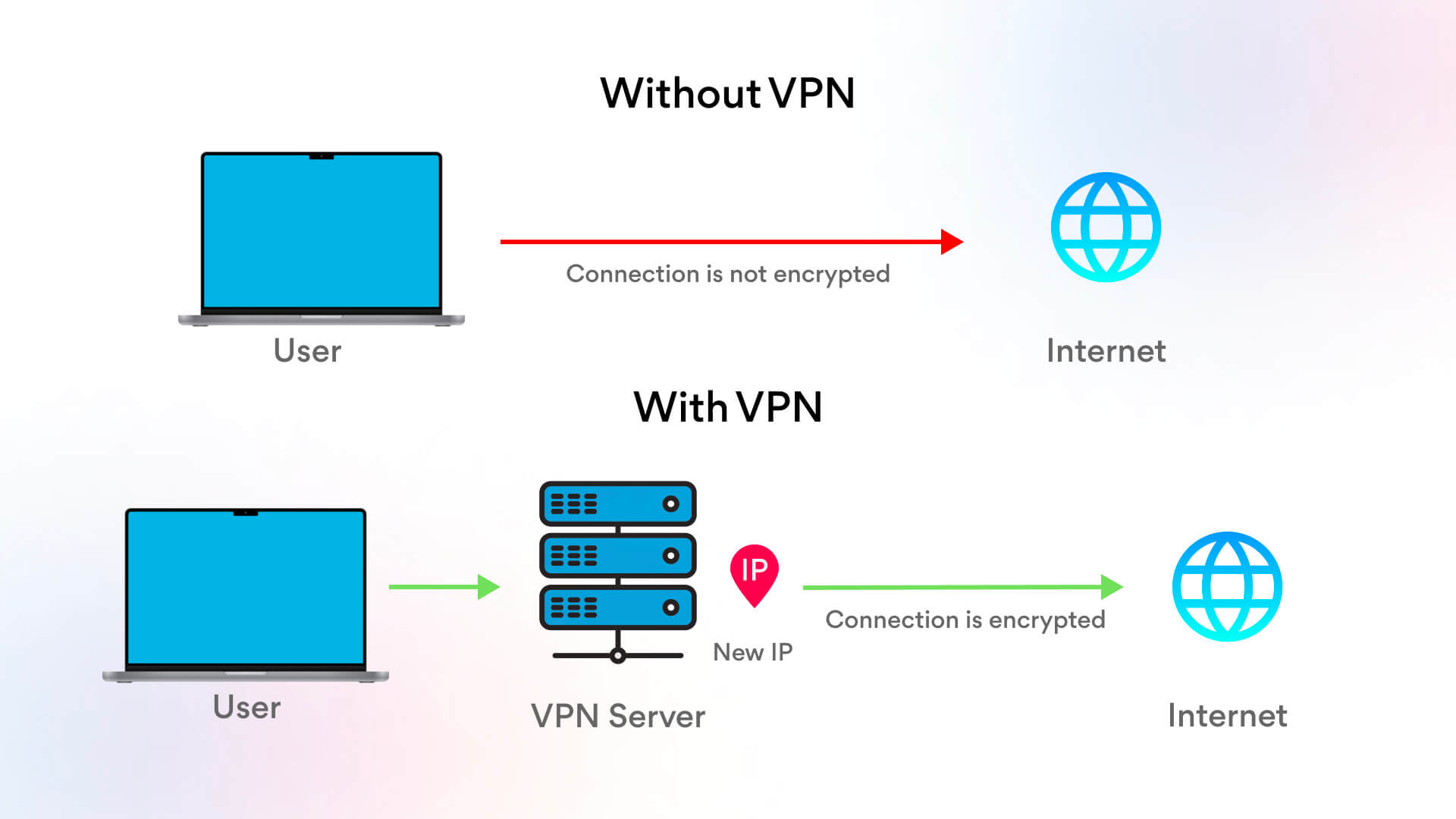
A VPN allows users to safely access an internal network as it provides an encrypted connection. It is a useful option for all remote users to access internal communication systems.
All the devices that have direct access to the company’s network must be protected using endpoint security software. Endpoint protection includes antivirus software, firewalls, intrusion detection/prevention systems (IDPS), and endpoint detection and response (EDR) tools.
By following the given best practices, organizations can significantly enhance the security of their internal communications:
Ensure the software applications are regularly updated to overcome potential glitches and vulnerabilities. Here, it is also important to pick software providers that provide regular system updates and security patches.
It is essential for all applications, including operating systems, communication platforms (like email clients and messaging apps), antivirus software, firewalls, and other tools.
Your company’s employees must be aware of the latest security threats and vulnerabilities. They must be trained about their role in maintaining a secure communication environment. Implement interactive workshops and role-based training, and provide periodic training to keep them informed.
Regular audits and monitoring will help to identify potential threats before they cause severe harm. Review access logs to detect unauthorized entry attempts, conduct regular compliance audits, and analyze traffic patterns to check for any suspicious activity.
Establish clear company policy and security guidelines regarding data handling. A clear policy will allow employees to understand their role in data security. The policy information is openly available to the employees to ensure clear communication. A dedicated team should be appointed to review periodically and update the policies to cover loopholes and new regulatory requirements.
Enforce rules for regularly updating and selecting stronger passwords. It reduces the risk of unauthorized access due to stolen or compromised passwords. Set a password expiry policy after a specific period of time to ensure regular updates. Strengthen password selection requirements (e.g., a mix of letters, numbers, symbols, and a minimum length).
Additionally, train employees to secure passwords and avoid reusing the same password over multiple platforms.
Securing internal communication is crucial for any organization that values privacy, trust, and smooth operations. To maintain this security, businesses must conduct regular audits and reviews, keeping systems like ISME effective. Strong encryption, multi-factor authentication, role-based access control, and audit trails all play a key role in safeguarding data and ensuring smooth communication.
Prioritizing these steps protects your organization from threats and strengthens your communication network, supporting growth and maintaining your reputation.




Nov 20 2024
8 min read

Feb 8 2024
4 min read

Jan 17 2024
4 min read

Jul 18 2025
9 min read
Take complete control of what you show on your digital signage & how you show it.
Start Free Trial Schedule My Demo